Cybersecurity - DEEP
Cybersecurity
The essential evolution of SOCs towards a hybrid mode
With the constant evolution of digital environments, POST is transforming its SOC into a hybrid by combining several technological advances.
Read this articlePublished on
08 August 2023
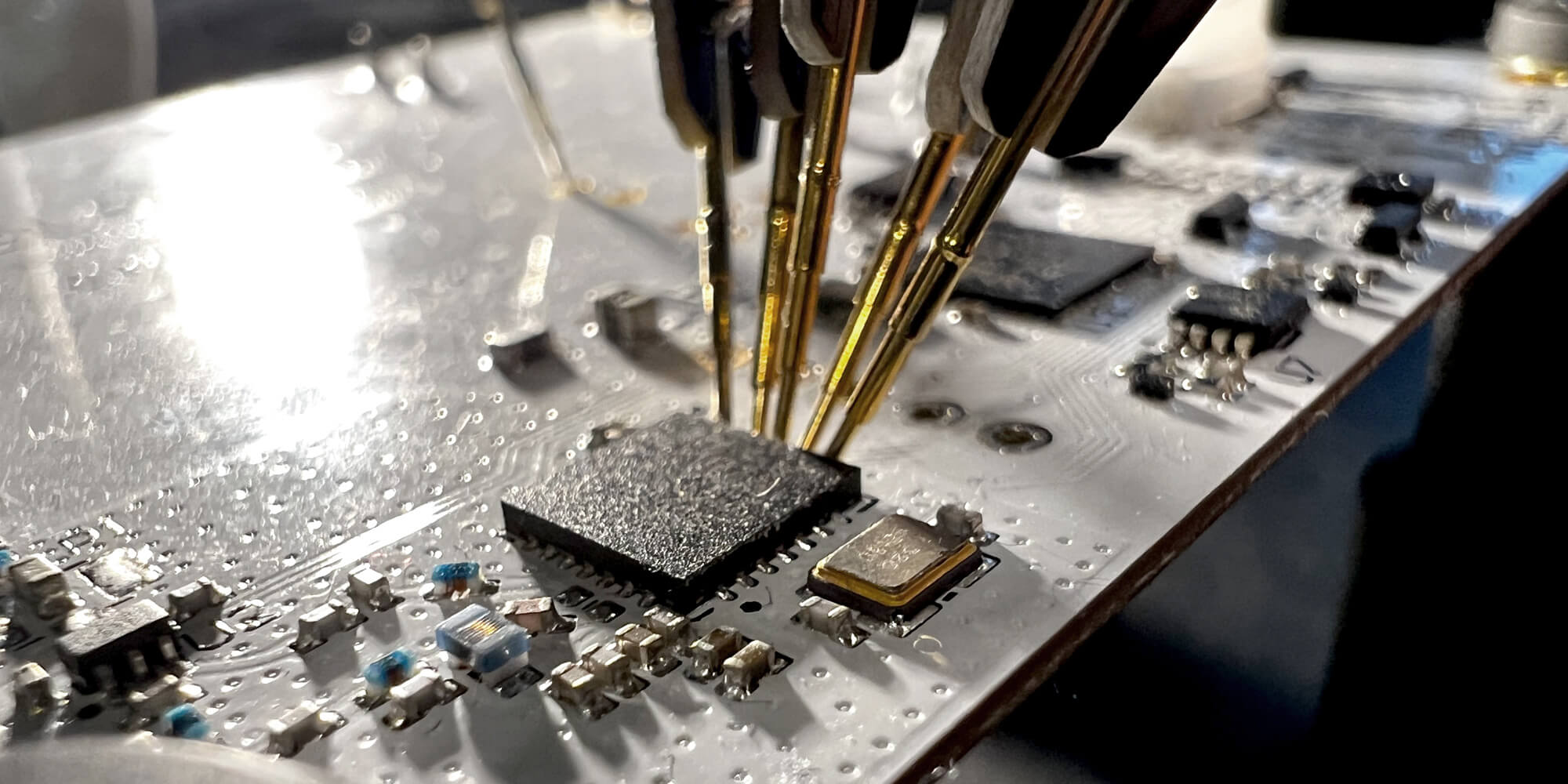
Searching for vulnerabilities in IoT devices: Case of CVE-2022-46527 (Part 2)
This article is the second part of case study CVE-2022-46527 and will discuss the discovery of the vulnerability and a proof of concept leading to a crash
Read this articlePublished on
26 June 2023
Searching for vulnerabilities in IoT devices: Case of CVE-2022-46527 (Part 1)
Setting up the environment to scan IoT devices for vulnerabilities: Case of CVE-2022-46527
Read this articlePublished on
14 March 2023
Contact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?