20,000 phishing SMS posing as Guichet.lu detected in one week - DEEP

Are you one of the people who recently received an SMS claiming to have come from Guichet.lu and inviting you to claim your right to a tax rebate of as much as several hundred euros? In recent weeks, an extensive SMS phishing campaign has targeted Luxembourg mobile numbers, pretending to be the Public Administration citizens’ portal. As often with this type of attack, the goal of cyber criminals is to retrieve data, such as user names, passwords, authentication codes, which they can then use to extort money from you.
Between 1,500 and 6,000 phishing attempts every day
Using its tool Telecom Intrusion Detection System (TIDS) developed by its CYBERFORCE department, DEEP was able to carry out an in-depth analysis of this phishing attack that stole Guichet.lu's identity.
In the first week of January, we detected some 20,000 fraudulent SMS text messages allegedly sent on behalf of the public portal and passing through our mobile network. In recent weeks, between 1,500 and 6,000 of these messages have been sent daily to Luxembourg mobile numbers from various foreign platforms. These messages invite you to click on URLs containing the words ‘guichet,’ ‘my-guichet’ or ‘lux’ with the aim of duping the user.
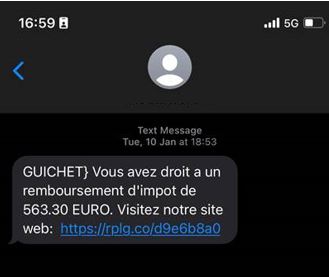
Example of fraudulent SMS:
The fact that the senders of the messages and the phishing websites to which links are redirected change continuously makes these attacks particularly difficult to identify and thwart.
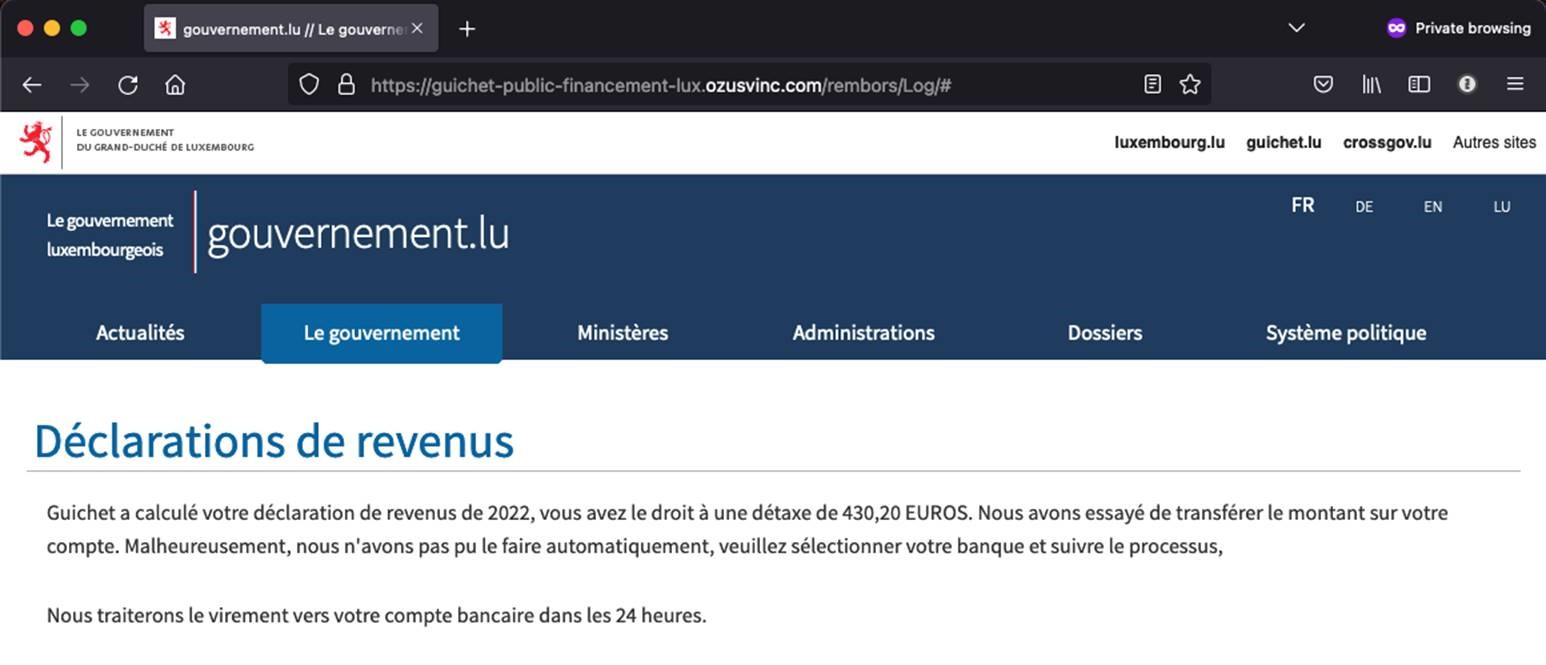
Example of malicious website:
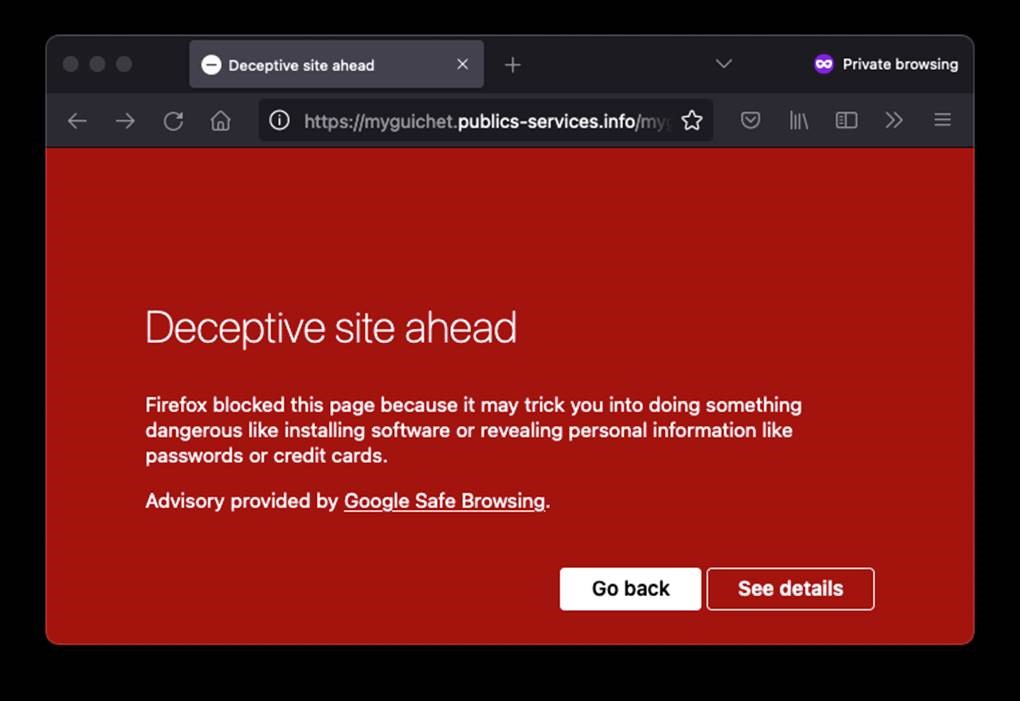
Example of Website blocked by Google Safe Browsring:
A unique tool for detecting fraudulent SMS
To provide a response to this fraud, the detection of these attacks inside TIDS deployed by the CYBERFORCE team uses machine learning. It analyses the content of messages passing through DEEP network in order to detect fraud attempts. The approach is fully automated. Using artificial intelligence technology, the confidentiality of content can be guaranteed while this surveillance is carried out.
The tool raises an alert for each fraudulent phishing message. Subsequent messages having the same/similar content can then be blocked by DEEP. As part of this recent campaign, and despite being under no obligation to do so, the team made sure that many of these messages were blocked, as far as the resources available permitted. However, it was not possible to block every message, and unfortunately some reached the end users.
Very convincing attacks
This campaign, in which the attackers pose as Guichet.lu, is not an isolated one. In recent years, malicious groups have been passing themselves off as large Luxembourg organisations, including well established Luxembourg banks, LuxTrust, DEEP, or other service providers for citizens, in order to steal data or, worse still, money from users.
These attacks demonstrate a deep understanding of the Luxembourg ecosystem and its stakeholders. Some fraudulent SMS text messages were sent in Luxembourgish. Sites to which fraudulent links refer reproduce the environment of the web portals of the organisations whose identity the attackers have assumed.
Detecting and blocking messages that usurp your identity
In order to help organisations whose clients are deceived by these campaigns, DEEP provides a dedicated service, ensuring that SMS phishing campaigns targeting the clients are detected and promptly handled. This helps reduce support effort and improve customer experience to the organisations.
In addition to blocking malicious SMS before they reach the user, the service also blocks its sender. What is more, steps are being taken to inform relevant cyber-incident handling teams about the website via which cyber criminals attempt to retrieve connection data. Their hosting service of the website is notified, and the domain name is reported as being used for criminal activities. DNS services are also informed to about malicious domains. Finally, the team also warns web browser creators to include incriminated phishing websites in existing anti-phishing devices. These various measures help to counter attacks.
Preventing risks
Even though these attackers are beyond the control of the organisation whose identity has been usurped, it still has to suffer the consequences. A bank’s customer whose money has been stolen as a result of a phishing campaign will necessarily contact customer service, which will have to devote resources to it and, where appropriate, compensate the customer if fraud can be proved. Preventing such attacks through DEEP services minimize the exposure to such unpleasantness and avoids the risk of users’ confidence in a bank, administration or organisation being damaged.
We must remain vigilant
Lastly, users should be reminded to be cautious about text messages or emails asking them to log in and provide information. Most organisations or administrations NEVER directly invite beneficiaries of their services to connect via an Internet link sent by SMS or email. In general, it is recommended that you never click on a link that is sent to you unless this is in connection with something that you yourselves have initiated (for instance, a password renewal). When in doubt, do not click, and consult your provider using a formal access channel.
Contact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Cybersecurity
DDoS attacks in Luxembourg in 2024
Discover the statistics of DDoS attacks detected in Luxembourg in 2024 by POST Cyberforce.
Published on
31 March 2024
DDoS attacks in Luxembourg in 2023
Discover the statistics of DDoS attacks detected in Luxembourg in 2023 by POST Cyberforce.
Published on
15 February 2023
DDoS attacks in Luxembourg in 2022
Discover the statistics of DDoS attacks detected in Luxembourg in 2022 by POST Cyberforce.
Published on
11 October 2022