Telecom Security - DEEP
Telecom Security
Discover our Telecom Intrusion Detection System (TIDS) and Telecom Security Scanner (TSS) solutions. Solutions developed by a telecom operator for telecom operators.


Perfect for:
Telecom Intrusion Detection System
An innovative solution that combines advanced detection, threat intelligence, automation and flexibility to defend the critical core network assets.
Your daily threat analysis in seconds
Investigating location tracking or call interception attacks ? TIDS aims to quickly identify the threat actor, the targeted subscriber and to analyse tactics
and techniques used to attack your signalling network.
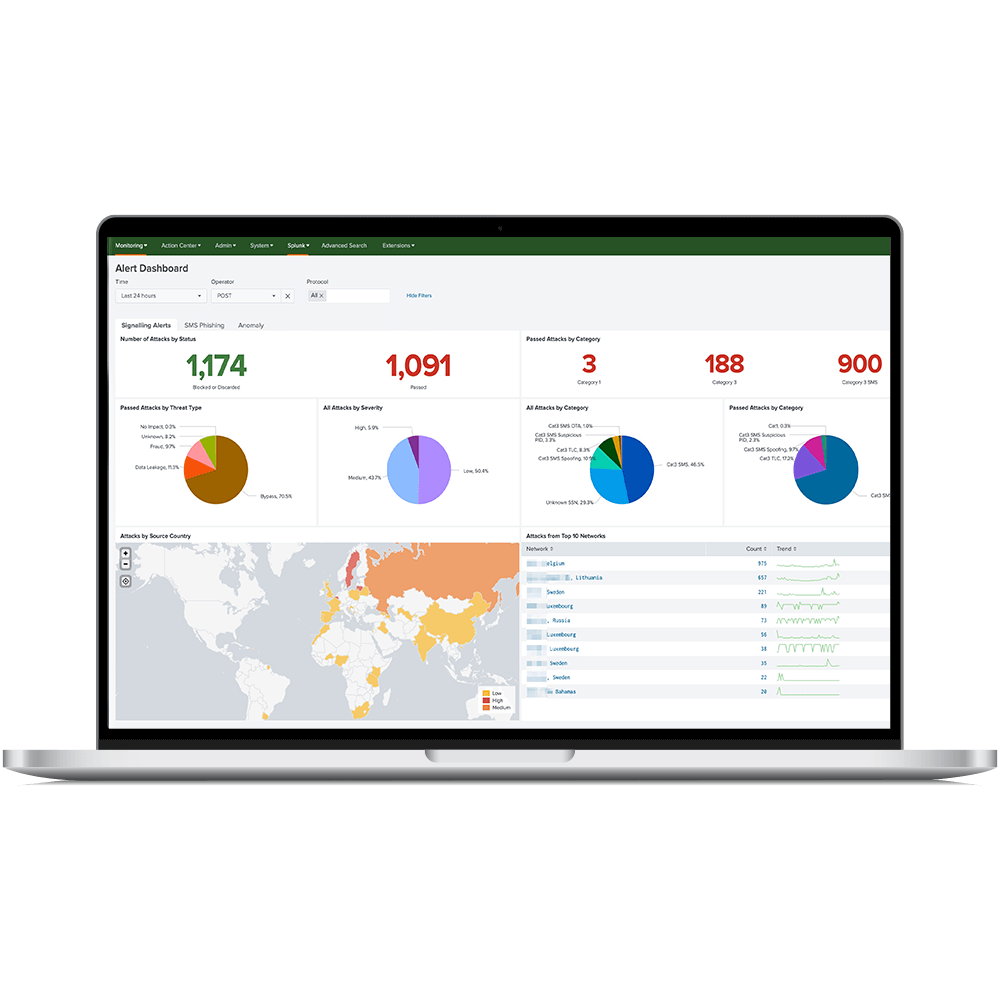
Getting back the control over signaling threats
Advanced Detection
Powered by a large ruleset and AI/ML models, TIDS discovers the unexpected by tracking every single signalling messages to detect new attack patterns.
Threat Intelligence
Surveillance companies or Government agencies, these threat actors have to be tracked, identified and tackle promptly.
Smishing
SMS phishing and propagation of malware via SMS became standard to extort subscribers and steal sensitive information.
Cross Protocols
Attackers often use several protocols to carry their attacks, going from SS7 to Diameter in seconds. Identifying cross-protocol attacks helps faster threat
detection.
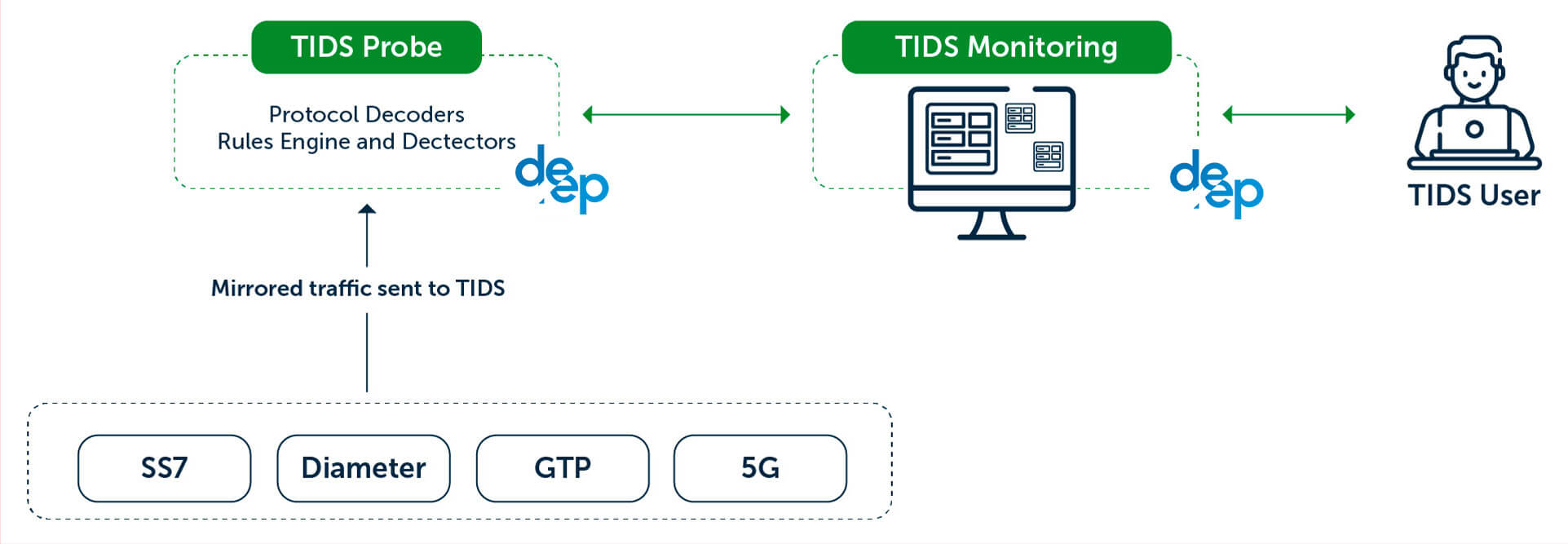
How TIDS fits in your network
TIDS is a full software solution aggregating mirrored traffic from different points in the network to ensure 360° visibility.
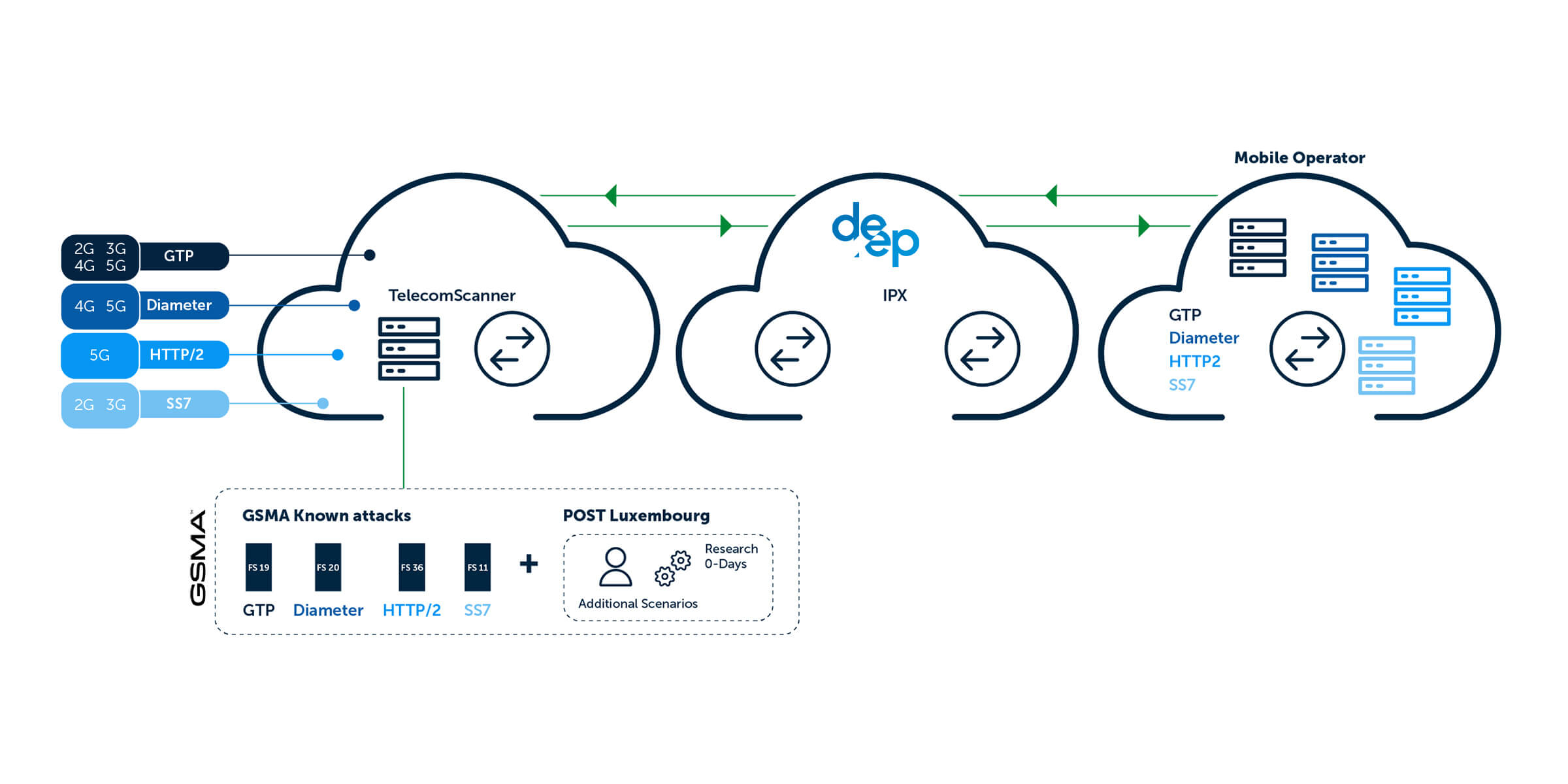
Telecom Security Scanner
The best defence is attack, using the attackers mindset allows us to discover new vulnerabilities, best in a real scenario the mobile core network of mobile operators accross the world. This helps MNO to understand their weaknesses and fix them before threat actors exploit them.
Attacking all technologies from 2G to 5G
Telecom Security built by a telecom operator for telecom operators
SS7
2G/3G signalling abusing MNOs on interception, location tracking, fraud or bypass
Diameter
4G signalling abusing MNOs on interception, location tracking or bypass
GTP-C
2G to 4G abusing MNOs on Denial of Service, data gathering, exploitation of infrastructure and DNS
5GC
5GC bringing more security but still vulnerable to many threats
How TSS is setup to attack your network?
All our attacks are launched from Luxembourg from nodes connected to POST Luxembourg production signalling network reaching more than 400+ operators worldwide.